APPROACHES, TOOLS AND TECHNIQUES FOR SECURITY TESTING

INTRODUCTION TO SECURITY TESTING
Security testing is a process that is performed with the intention of revealing flaws in security mechanisms and finding the vulnerabilities or weaknesses of software applications. Recent security breaches of systems at retailers like Target and Home Depot, as well as Apple Pay competitorCurrent C, underscore the importance of ensuring that your security testing efforts are up to date.
The prime objective of security testing is to find out how vulnerable a system may be and to determine whether its data and resources are protected from potential intruders. Online transactions have increased rapidly of late making security testing as one of the most critical areas of testing for such web applications. Security testing is more effective in identifying potential vulnerabilities when performed regularly.
Normally, security testing has the following attributes:
- Authentication
- Authorization
- Confidentiality
- Availability
- Integrity
- Non-repudiation
- Resilience
WHY SECURITY TESTING
System testing, in the current scenario, is a must to identify and address web application security vulnerabilities to avoid any of the following:
- Loss of customer trust.
- Disturbance to your online means of revenue generation/collection.
- Website downtime, time loss and expenditures in recovering from damage (reinstalling services, restoring backups, etc.)
- Cost associated with securing web applications against future attacks.
- Related legal implications and fees for having lax security measures in place.
CLASSES OF THREATS
Here are the different types of threats which can be used to take advantage of security vulnerability.
Privilege Elevation
Privilege elevation is a class of attack where a hacker has an account on a system and uses it to increase his system privileges to a higher level than he/she was not meant to have. If successful, this type of attack can result in a hacker gaining privileges as high as root on a UNIX system. Once a hacker gains super-user privileges, he is able to run code with this level of privilege and the entire system is effectively compromised.
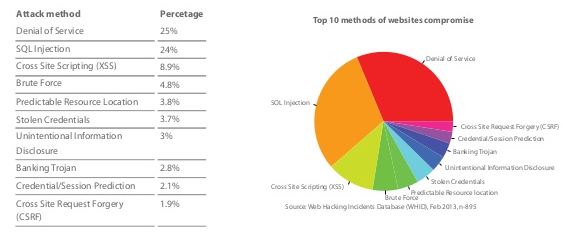
SQL Injection
SQL injection is the most common application layer attack technique used by hackers, in which malicious SQL statements are inserted into an entry field for execution. SQL injection attacks are very critical as an attacker can get critical information from the server database. It is a type of attack which takes the advantage of loopholes present in the implementation of web applications that allows a hacker to hack the system. To check the SQL injection we have to take care of input fields like text boxes, comments, etc. To prevent injections, special characters should be either properly handled or skipped from the input.
Unauthorized Data Access
One of the more popular types of attacks is gaining unauthorized access to data within an application. Data can be accessed on servers or on a network.
Unauthorized access includes:
- Unauthorized access to data via data-fetching operations
- Unauthorized access to reusable client authentication information by monitoring the access of others
- Unauthorized access to data by monitoring the access of others
URL Manipulation
URL manipulation is the process of manipulating the website URL query strings & capture of the important information by hackers. This happens when the application uses the HTTP GET method to pass information between the client and the server. The information is passed in parameters in the query string. The tester can modify a parameter value in the query string to check if the server accepts it.
Denial of Service
A denial-of-service (DoS) attack is an explicit attempt to make a machine or network resource unavailable to its legitimate users. Applications can also be attacked in ways that render the application, and sometimes the entire machine, unusable.
Data Manipulation
In data manipulation, a hacker changes data used by a website in order to gain some advantage or to embarrass the website’s owners. Hackers will often gain access to HTML pages and change them to be satirical or offensive.
Identity Spoofing
Identity spoofing is a technique where a hacker uses the credentials of a legitimate user or device to launch attacks against network hosts, steal data or bypass access controls. Preventing this attack requires IT-infrastructure and network-level mitigations.
Cross-Site Scripting (XSS)
Cross-site scripting is a computer security vulnerability found in web applications. XSS enables attackers to inject client-side script into Web pages viewed by other users and trick a user into clicking on that URL. Once executed by the other user’s browser, this code could then perform actions such as completely changing the behavior of the website, stealing personal data, or performing actions on behalf of the user.
All of the attacks listed above are most critical threat classes but these are not all.
SECURITY TESTING TECHNIQUES
To prevent all of the above security testing threats/flaws and perform security testing on a web application, it is required to have good knowledge of the HTTP protocol and an understanding of client (browser) – server communication through HTTP. Also, basic knowledge of SQL injection and XSS is required. The following techniques will help in performing quality security testing:
Cross Site Scripting (XSS):
The tester should additionally check the web application for XSS (Cross site scripting). Any HTML e.g. or any script e.g.
Không có nhận xét nào:
Đăng nhận xét